The NightOwl application has existed since 2018 and is used to automatically switch between light/dark modes on the operating system. It is an alternative to the built in macOS automatic mode which only switches when the user steps away from the computer.
However, the application has been bought out by “TPE.FYI LLC” in late 2022 that forcibly joins your devices into a botnet for use of market research, without your knowledge (other than the TOS in small text on the download page) or express consent (this feature cannot be turned off, even when the app is quit). This is documented in their terms of service.
This is extremely shady. How do I know if other apps I have are making me part of a botnet?
Use free and open source software
Something being open source doesn’t automatically make it safe to use. Sure, it means it’s easier for people to check for security issues, but how many people actually have the knowledge and the time to do it? And even then, take the log4j vulnerability from a while ago, it’s been present in the code since 2013 and only reported in like 2021.
Common sense still prevails. Don’t install obviously shady freeware. Something like GIMP or Blender or Ubuntu or FreeCAD or ProjectLibre is going to be safe. Large community = most likely safe.
FOSS isn’t generally vulnerable to the “buyout” vulnerability. It’s not new that a valuable browser extension is bought out and repurposed, but FOSS is less likely to fall to these bugs. (also fuck WEI. You’ll get more of this with WEI)
FOSS isn’t generally vulnerable to the “buyout” vulnerability.
Oracle has entered the chat.
You still need to build package and install it yourself though or else you are trusting someone else. Open Source software has been used as a vector for attacks before by bad actors getting access to the build system or source code.
I try to where I can, but unfortunately this is not always an option for me.
You need to examine your devices packets and see what servers they’re going to. You can do that through Wireshark on Windows, or use an external sniffer to examine them.
I’m not aware of any native apps for Mac that can do that, but maybe others will know.
You mean like Wireshark lol?
Didn’t know they maintained Mac packages as well, that’s great.
And Little Snitch and TripMode, and various other apps and *nix command line tools lol
If you’re just interested in connections (and don’t care about packet inspection) you can use Little Snitch (paid) or LuLu (FOSS).
Actually, all the Objective-See Foundation security tools are great and target specific classes of vulnerabilities, like LuLu for outgoing network connections, RansomWhere for detecting ransomwear by looking for encryption events, Oversight that monitors you cameras and microphones and a bunch of other really small, but really useful security utilities. Better than running a shady antivirus that’s going to suck up loads of resources and rely on signatures.
+1 for Objective-See
PiHole on a Raspberry Pi
When I’m using VPN, my pihole can’t see the traffic, and won’t be able to block any ads or analyze the traffic. Also, some browsers use their own DNS, so the pihole can’t block that traffic either.
Other than that, the pihole is a great tool to figure out what’s going on in your network. That’s how I found out that an Android phone is super noisy in my netwrok. Then I installed LineageOS+gapps, and it got better. It was still a bit noisy, so I reinstalled LineageOS, but this time without gapps and no play store. It finally got to the level I like, but unfortunately the world around me wasn’t compatible with this phone any more. :( But anyway thanks to pihole, I was able to figure out what kind of changes I need to make so that I’ll get the level of privacy I’m happy with.
Are you using the VPN locally on your device or router level?
On the device level at this point. AFAIK, my VPN isn’t designed to work on a router level.
Anyway, it makes sense that once you encrypt the traffic, the pihole won’t be able to see what’s going on.
Wireshark is available on intel and arm macs.
Vigilance. Resource monitoring and network traffic monitoring. The occasional scan with anti malware tools to catch known bad actors.
I use malwarebytes when someone needs a scan, though they got naggy enough that I uninstalled it right after using it for my grandfather. Other monitoring IDK. LittleSnitch is popular on Mac but I have no personal experience with it.
Read all the TOS?
Disclaimer : not an Apple user, not a lawyer
This should be illegal by European law. Without further knowledge it seems like a prime example for the GDPR letter of death and a pretty solid case for data protection lawyers
Unannounced changes to the Terms of Service are definitely illegal.
But various forms of backstabbing are legal as long as you let your users know that the TOS have changed. I mean, who reads that stuff anyway. You can literally throw in there whatever you like and people will just click “I agree” regardless.
This is right. In the modern day, people likely receive dozens of emails each year informing them of changes to some terms of service or another. When most can’t be bothered to read those updates for absolutely crucial applications, how many would be expected to read an update for a small-time utility app that they might even forget they had?
I get those from my bank, insurance company and some other places too. I trust that their brand isn’t disposable, so they probably aren’t going to do anything too sneaky.
However, some random app from a random developer you never heard of is a different story. All of that is 100% disposable, so reputation is meaningless to a scam operation like that. Once they get your money, the company suddenly goes bankrupt and the developers disappear forever.
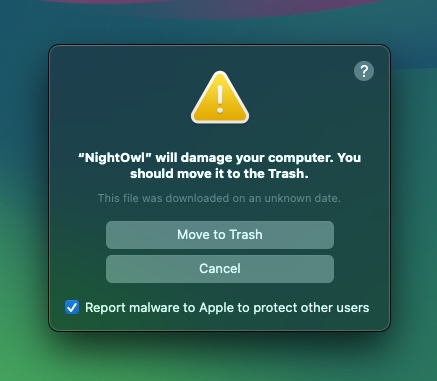
When did this message appear?
Should be illegal
Light and dark mode can be set to turn on automatically at a given time or can be set via sunset/sunrise. Not sure where you got people need to step away from their devices to enable.
Jeez. I’ve been using it since 2018 and is one of my favorite applications. Maybe downloading an older functional version would mitigate this?
I don’t use a Mac but can’t you just block the app from accessing the internet in your firewall? MacOS has a firewall, right?
The macOS firewall can only block incoming connections. If you want to block outgoing too you need something like LittleSnitch or LuLu.
It does. Didn’t think of that actually.













